Uninterrupted operation of IT systems stands as the ultimate goal for data center managers. The value of a data center facility is intrinsically linked to its functionality. In today’s modern landscape, data centers are the backbone of business, banking, and government operations, processing vast amounts of data. Environmental factors significantly influence the performance of IT hardware, including power supplies, cooling systems, and colocation providers. The choice of a data center provider with redundant backup systems is critical, making the exploration of N-Modular redundancy paramount.
Dependable IT: A Competitive Edge:
-
Improvement in fault tolerance of the IT facility
Understanding Redundancy:
N-Modular redundancy, specifically N + 1 and N + 2, plays a pivotal role in bolstering IT system reliability. These levels of redundancy provide varying degrees of backup, ensuring the seamless operation of the system even in the face of failures. The different redundancy levels are as follows:
- N Redundancy: The baseline number of existing IT units constitutes N, representing the minimum required components for system operation. However, this level lacks redundancy, leading to system shutdown in case of failure.
- N + 1 and N + 2 Redundancy: Incorporating a single backup unit (N + 1) or two separate backups (N + 2) increases reliability. These setups allow the system to continue functioning during the failure of a particular unit, with N + 2 redundancy providing an additional layer of backup for exceptional cases.
- 2N, 2N + 1, and 2N + 2 Redundancy: These levels are built upon the baseline capacity of N. 2N redundancy implies doubling the baseline capacity, with an equal number of backup units. The 2N + 1 and 2N + 2 configurations offer further redundancy by including additional backups, ensuring optimal uptime.
- 3N/2 and 4N/3 Redundancy: Derived from the IT system’s baseload, these levels allocate redundancy capacity to ensure consistent system operation even under partial load. This approach is particularly crucial for components like power supply systems.
Benefits and Considerations of Redundancy:
Redundancy, particularly N-Modular redundancy, enhances reliability and availability in IT systems. However, considerations for component failure rates and workload stress are necessary when selecting appropriate redundancy levels. Mismatched backup components can lead to performance fluctuations, impacting the system’s long-term effectiveness.
Choosing the Right Redundancy Configuration:
Selecting the suitable configuration is crucial when implementing redundancy methods. Active, passive, and load-sharing configurations offer distinct approaches to maintaining system functionality during failures. The choice depends on factors such as user requirements, cost, resources, and compliance.
Monitoring and Maintenance for Optimal Performance:
Maintenance and monitoring play a pivotal role in ensuring the reliability of redundant components. Advanced monitoring solutions, like AKCP’s comprehensive technologies, enable real-time tracking of individual components and the entire IT facility. By proactively addressing issues, downtime risks are minimized, leading to more reliable IT operations.
Conclusion:
N-Modular redundancy is a cornerstone of IT system reliability, safeguarding operations against failures and unforeseen events. The various redundancy levels and configurations offer flexibility and scalability to meet diverse operational needs. As businesses continue to rely on IT systems for their operations, understanding and implementing effective redundancy strategies like N-Modular redundancy are essential for sustainable success.
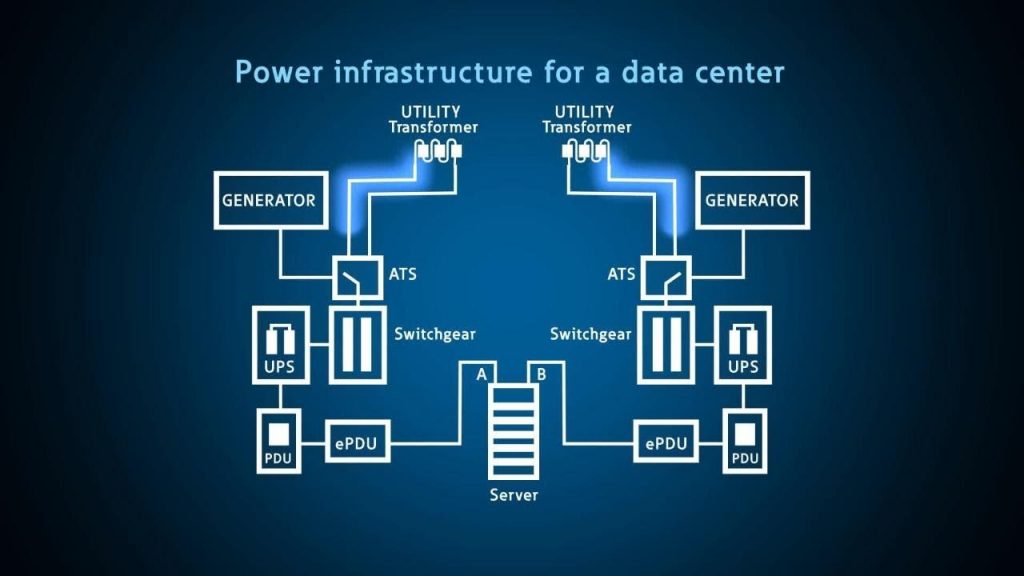
Photo Credit: EatonVideos Youtube Channel





