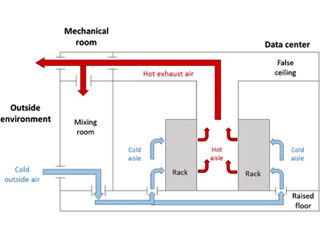
This form of monitoring is to provide operators with peace of mind by warning them of issues caused by failure or human error. Despite the benefits, monitoring alone will leave operators and engineers with blind spots. In fact, relying on technology could expose operators to downtime and poor performance.
1. You Can’t Monitor Everywhere
2. You Can’t Monitor Resilience
3. You Can’t Monitor the Future
Overcoming Blind Spots
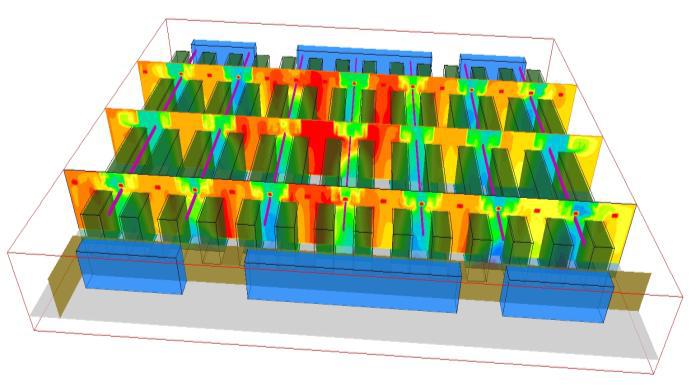
Photo Credit: arcofluid.fr
So, how can operators get around these constraints? The solution is to combine tools that tell you about the past and present conditions. One of these might be the key to let you predict how the environment will behave in the future. This necessitates the use of Computational Fluid Dynamics (CFD). CFD-based simulation is a virtual simulation of a complete data center. This allows operators to compute the facility’s environmental conditions. Virtual sensors, for example, ensure that the simulated data is accurate. As a result, the findings can be utilized to analyze circumstances at any location in great depth.
In addition to temperature maps, CFD includes humidity, pressure, and airspeed. Airflow, for example, is traced to show how it flows from one point to another. This simple monitoring gives researchers unique insight into the origins of thermal problems.
Network and Cloud Blind Spots
After we have discussed the blindspots in the physicality of a data center, let’s now turn our attention to network and cloud blindspots. As network blind spots were first to worry in traditional network designs, and a critical component of platform visibility, monitoring, and security since then.
List of Network Blind Spots
It would be fruitless to attempt and compile an entire list of network blind spots because there are several scenarios and technical specifics that could be the genesis of a blind spot.
In any event, it could be useful to categorize network blind spots in order to provide a revision guide.
1) Related to Your Network Management
Network platforms are evolving, new offices are opening, new hardware is being installed, new services are being offered, and new communication linkages are being utilized.
Platforms are also growing more sophisticated, new virtual network outlines can be introduced, cloud services can be utilized, and new bandwidth control outlines can be developed.
You must keep in mind that each new item you add, no matter how insignificant it may appear, may trigger a network blind spot.
This necessitates platform managers to avoid any blind spots.
We’ve come up with a couple of examples of blind spots that fall under this category:
- Remote offices with a view of the required visibility outline for the components.
- Traffic is encrypted without inspection, presuming it is secure web traffic.
- Hardware device configuration for easier use.
- SPAN ports that have been misconfigured may be causing a significant level of latency or discarding valuable traffic for analysis.
- Inconsistencies in workstation configuration. Protocol configuration, IP addressing design, DNS service, download standards, and software installation, among other things, are all different.
- There are flaws in the software update process for the network’s devices.
2) Related to the Server Virtualization Outline
Photo Credit: pandorafms.com
Any virtualization technique that is introduced generates traffic between servers, which is commonly referred to as east-west traffic, which can escape from a visualization outline whose design is based on physical servers connected to a network.
Consider a physical server in which you’ve set up many servers that communicate with one another to provide a specific service.
If your users are experiencing performance issues, it may be impossible to diagnose the problem without considering the virtualization architecture, as the fault could be in the traffic between two virtual servers.
Traffic that never reaches a physical port on your platform and so falls outside of the visibility outline’s scope.
Virtualization, on the other hand, is connected with a development plan that involves rapidly generating and destroying virtual servers.
In order to eliminate any potential blind areas, an appropriate visibility outline must be customized to server formation and removal speeds.
3) Related to the Mobile Workforce
Every day, an increasing number of workers have access to and interact with data stored on the corporate network or in the cloud, using Internet-connected devices that are not part of the traditional network platform.
Integrating These Devices Entails An Additional Security Risk
In reality, ComputerWeekly magazine released the findings of a poll of 500 IT executives from various companies in March. 92% of those polled expressed concern about the security risks posed by a mobile workforce.
Apart from security concerns, visibility and monitoring of these devices, which are connected from homes, Internet cafés, or airports and are both corporate and personal in nature, becomes increasingly difficult.
Because the communications service features may be the problem, the performance evaluation for these users, for example, tends to be tough to deal with failure reports.
4) Related to Wireless Networks
Wireless technology’s integration into wired network infrastructures has created a slew of possible blind spots.
Wireless networks indicate the addition of several mobile devices that are not bound by the company’s security policy.
This situation could get considerably worse if the Bring Your Own Device (BYOD) policy is implemented.
Furthermore, these devices provide us with a new problem: illegal access points. It’s incredibly easy for a device to become the entry point for a whole slew of other devices, some of which may not even be physically present on the platform.
How Should Network Blind Spots Be Dealt With?
A basic step is to raise awareness of the need of defining a visibility architecture as well as a good monitoring platform.
Then, in large businesses, you develop a corporate communication process on the subject so that departments that may be operating in isolation, such as Systems Development, Platform, Technical
Afterward, you should be able to evaluate the possibility of incorporating the following corporative procedures:
- A network audit is an intriguing alternative for early blind-spot discovery, but due to the time and labor required to complete it, it is often postponed or even unscheduled.
- To enforce a strong security data policy that includes, user profile management, password complexity requirements, VPN connections for remote workers, multiple usernames and password checks, restrictions on wireless network access, access control to each device’s administrator passwords, and so on.
- Reporting the company’s security rules to key people, in order to foster an environment where security is seen as a shared responsibility.
There are numerous tasks to be completed in the technical field. Let’s have a look at a few of them:
- Creating data-gathering techniques that cover the entire platform.
- AKCPro Server includes several features aimed to achieve this goal. Among them, the satellite server that enables centralized monitoring of thousands of allocated devices.
- Maintaining a network map that includes all functioning elements, including wireless network components.
- Using the acquisition-of-more-convenient-information outline, define an outline that is flexible enough to monitor any network element.
- Establishing user experience monitoring techniques, which will inevitably bring us to each of the operating platform elements: firewall, switches, web servers, application servers, database servers, communication links, cloud services, etc.
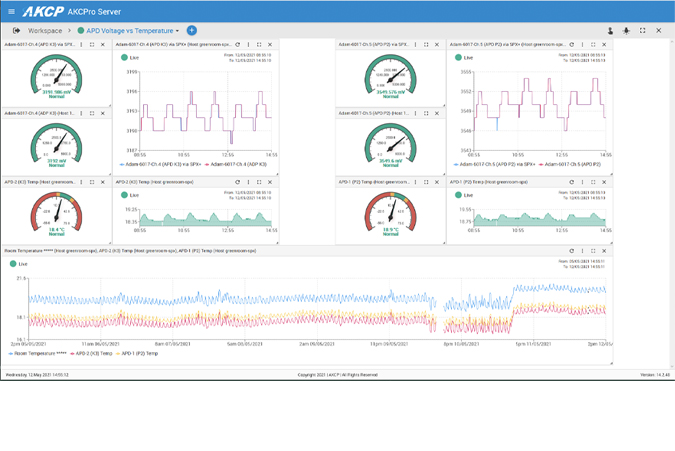
AKCPro Server
AKCPro Server is our world-class central monitoring and management software. Suitable for a wide range of monitoring applications. Free to use for all AKCP devices. Monitor your infrastructure, whether it be a single building or remote sites over a wide geographic area. Integrate third-party devices with, Modbus, SNMP, and ONVIF compatible IP cameras.
All deployed AKCP base units and attached sensors can be configured and monitored from AKCPro Server (APS). Base units communicate with the server through your wired local network (LAN) or wide area network (WAN). Remote sites with no wired network send data to the server through the cellular data network via a VPN connection.
Wireless Thermal Map
Wireless thermal mapping of your IT cabinets. With 3x Temperature sensors at the front and 3x at the rear, it monitors airflow intake and exhaust temperatures, as well as providing the temperature differential between the front and rear of the cabinet (ΔT) Wireless Thermal maps work with all Wireless Tunnel™ Gateways.
Conclusion
Monitoring and CFD are complementary rather than competing technologies. Each supplies data center operators with critical performance and blind area information. They do provide total visibility into not how your data center is performing today, but also how it will perform tomorrow.